
Stay Informed, stay vigilant: The Significance of Cyber Threat Intelligence
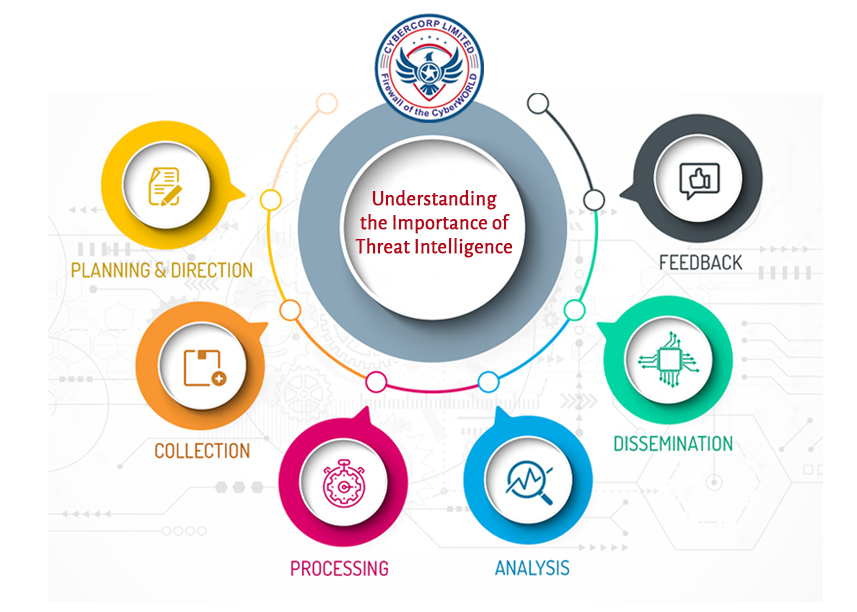
In today’s digital world, understanding and defending against cyber threats is more important than ever. As someone deeply involved in cybersecurity, I’ve witnessed firsthand how crucial Cyber Threat Intelligence (CTI) is for safeguarding our digital assets. Let me walk you through why CTI matters and how it can make a significant difference in protecting your organization.
What is Cyber Threat Intelligence?
Cyber Threat Intelligence refers to the information organizations use to understand potential threats and vulnerabilities in their digital environment. It includes data about threat actors, their tactics, techniques, and procedures (TTPs), and the potential impacts of various cyber threats. In essence, CTI helps organizations anticipate and prepare for cyber attacks before they happen.
Why is Cyber Threat Intelligence Important?
-
Proactive Defense: Instead of waiting for a breach to occur, CTI enables you to be proactive. By analyzing threat data, you can predict and prepare for potential attacks. For example, if intelligence reveals that a specific type of malware is targeting your industry, you can take steps to strengthen your defenses against it.
-
Enhanced Incident Response: When a security incident does occur, having CTI at your disposal can streamline the response process. It provides valuable context, such as the origin of the attack, its likely impact, and the best response measures. This can significantly reduce the time it takes to contain and remediate the incident.
-
Improved Risk Management: CTI helps in assessing and managing risks more effectively. By understanding emerging threats, you can prioritize your security efforts and allocate resources where they are most needed. For example, if intelligence indicates an increase in ransomware attacks, you might focus on strengthening backup procedures and employee training.
-
Informed Decision Making: With accurate and timely threat information, you can make better decisions about your cybersecurity strategy. For instance, if CTI reveals that a new zero-day vulnerability has been exploited in the wild, you can prioritize applying patches and updates to protect against it.
Case Studies and Examples
Case Study 1: The 2020 SolarWinds Attack
One of the most notable examples of CTI in action is the SolarWinds cyber attack. The attackers used sophisticated techniques to compromise SolarWinds’ software and gain access to numerous high-profile targets. Organizations that had robust CTI capabilities were able to detect unusual activity early and take steps to mitigate the damage. This underscores the importance of having up-to-date and actionable threat intelligence.
Case Study 2: The WannaCry Ransomware Outbreak
In 2017, the WannaCry ransomware attack affected thousands of organizations worldwide, encrypting files and demanding ransom payments. Organizations with strong CTI capabilities were able to quickly identify the ransomware’s behavior and deploy patches to stop the spread. This rapid response was crucial in limiting the impact of the attack.
How to Implement Effective Cyber Threat Intelligence
-
Gather Reliable Data: Start by collecting data from various sources, including threat feeds, security reports, and open-source intelligence. Ensure the sources are credible and relevant to your industry.
-
Analyze and Interpret: Analyze the collected data to identify patterns and potential threats. Use threat intelligence platforms or services that can help aggregate and analyze data efficiently.
-
Integrate with Existing Security Measures: Make sure the insights from CTI are integrated into your existing security systems and protocols. This includes updating firewalls, intrusion detection systems, and incident response plans.
-
Regular Updates and Training: Cyber threats are constantly evolving, so it’s crucial to keep your threat intelligence updated and ensure your team is trained to use it effectively.
Conclusion
In my experience, Cyber Threat Intelligence is a game-changer in the realm of cybersecurity. It shifts the focus from reactive to proactive defense, enhances incident response, and improves overall risk management. By leveraging CTI, you can stay ahead of emerging threats and better protect your organization’s digital assets. Investing in Cyber Threat Intelligence is not just a technical upgrade; it's a strategic advantage in today’s ever-evolving cyber landscape.
FAQs on Cyber Threat Intelligence
1. What is Cyber Threat Intelligence (CTI)?
Cyber Threat Intelligence (CTI) is information used to understand and anticipate cyber threats. It includes data about potential threats, such as the tactics and techniques used by attackers, and helps organizations prepare for and respond to these threats effectively.
2. Why is Cyber Threat Intelligence important?
CTI is important because it helps organizations proactively defend against cyber threats. By providing insights into potential threats and vulnerabilities, CTI allows for better preparation, quicker incident response, improved risk management, and informed decision-making.
3. How does CTI enhance incident response?
CTI enhances incident response by offering valuable context about a threat, such as its origin, behavior, and potential impact. This information helps security teams to quickly identify, contain, and remediate security incidents.
4. What are some examples of Cyber Threat Intelligence in action?
Examples include:
- The SolarWinds Attack: Organizations with strong CTI detected unusual activity early and took steps to mitigate damage.
- The WannaCry Ransomware Outbreak: Companies with effective CTI were able to identify the ransomware and deploy patches quickly to limit the attack’s spread.
5. How can I gather Cyber Threat Intelligence?
Gather CTI by collecting data from credible sources such as threat feeds, security reports, and open-source intelligence. Use threat intelligence platforms or services to aggregate and analyze this data.
6. How often should Cyber Threat Intelligence be updated?
CTI should be updated regularly to keep up with emerging threats and changes in the cyber threat landscape. Frequent updates ensure that your security measures remain effective against new and evolving threats.
7. How can CTI be integrated into existing security measures?
Integrate CTI by updating your security systems, such as firewalls and intrusion detection systems, with the latest threat insights. Also, incorporate CTI findings into your incident response plans and security protocols.
8. What are the main benefits of using Cyber Threat Intelligence?
The main benefits include proactive threat defense, enhanced incident response, improved risk management, and informed decision-making. CTI helps organizations anticipate and prepare for threats before they occur.
9. Can small businesses benefit from Cyber Threat Intelligence?
Yes, small businesses can benefit from CTI. Even though they may have fewer resources, CTI can help them understand potential threats, prioritize security efforts, and protect their digital assets effectively.
10. What tools or services are available for Cyber Threat Intelligence?
There are various tools and services available, such as threat intelligence platforms, security information and event management (SIEM) systems, and managed threat intelligence services. These tools help in collecting, analyzing, and acting on threat data.
Categories
Trending Posts
Why CyberCorp is not a mere SPAC?

We are

CoOperative Corporate
Creates a commonwealth among the partners
Cumulative Growth safeguards against losses to one entity
We believe in

Organic Growth
Promotes growth within the group companies
Ensures Maximum benefits
We do

Integration
Horizontal integration of the various products
Creating new and more effective scalable solutions
© 2022-2026 CyberCorp Limited. All Rights Reserved.



.png)






